Your IT Team Will Love Belden Horizon's Latest Security Updates

Your IT Team Will Love Belden Horizon's Latest Security Updates
Earlier this year, the National Security Agency issued guidance on how organizations can embrace a “Zero Trust” security model.
Put simply, this concept is predicated on the idea that security threats exist both inside and out of an organization, and that there shouldn’t be implicit trust in any part of the network (whether an employee or a device). It advocates for policies and systems that allow for continuous verification from more than one source.
It’s all very cheery, we know. But it’s a realistic view of what companies worldwide need to consider to increase network security, especially as many functions continue to be handled remotely.
How we’re helping Belden Horizon users move toward a ‘Zero Trust’ model
Belden Horizon is our remote connectivity service, and it aims to help you securely access your remote equipment – with no software or platform maintenance required on your part. Belden Horizon is designed to be SMART – Secure, Managed, Accessible, Reliable, Trusted – and the latest security updates to the service will help align it with your IT team’s objectives.
These updates are available for companies with Belden Horizon subscriptions through a Power User Plan or the use of the Persistent Data Network. The first update gives your organization the freedom to choose among three options for how logins are handled:
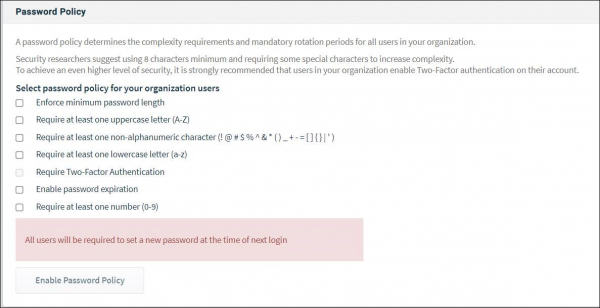
∙ The newest selection a company can make is to build and enforce their own password policy, including the option for two-factor authentication, which we highly recommend. Enforcing your own policy here is a simple process, in which you’ll choose password requirements. Your team will be familiar with this as well (who hasn’t put together a very specific mix of typed characters?):
∙ Another option that’s available is the existing Single Sign-On (SSO) selection. SSO allows for the same login credentials to be used securely across applications that employees use as a member of your organization. This option also allows for a more streamlined credential update in the case of new passwords or personnel changes.
∙ The third option is Belden Horizon's standard login process, which uses two-factor authentication.
These options for logging in essentially comprise Step 1 in a Zero Trust setup within Belden Horizon – the verification that the user needs to provide in order to log in to the service as a member of your organization.
Once the employee has logged in as a verified user, there’s Step 2 – you can ensure they have access to just what they need to see. This can be handled by your organization’s admin user, and may be set up as:
∙ Limited gateway access to prevent unwanted or unintentional access to additional assets
∙ Different levels of user access to prevent unwanted or intentional configuration changes
∙ Allowed IP settings to prevent unwanted or unintentional access to additional assets
A third step is verification that users are only accessing what they need to, when they need to. This is managed with the Virtual Lockout-Tagout (vLOTO™) feature, and it can also be used to control access for third-party vendors, including machine builders and system integrators.
Audit log updates
In addition to the updated login flexibility, we’ve also upgraded subscriber organizations’ audit log functions:
∙ Your organization’s audit log can now be exported on an automatic, regular cadence, and stored indefinitely. This information can be sent as a downloadable email to your organization’s administrator or as a CSV file to the SFTP server, and can be used if needed for future forensic analysis.
∙ The audit log can now also capture more information when users log in. Previously, the audit log captured the login ID and time. Now, the audit log can also note the user’s IP address and browser information, in the instance your IT security expert needs this information for forensic analysis.